As I know quite few of my vCloud Automation Center 6.x (lately renamed to vRealize Automation) customers are following my blog, I wanted to share this important information of a two different time bombs issues that affect the 6.x releases of the product. The purpose of this post is to highlight these two time bomb issues and the simple changes required to avoid them affecting the availability & manageability of your vCAC environment. If you have not done this or not sure if it was done during the installation time, please take the time to do it now. It is worth checking even if your environment was setup by a vCAC expert as it might have not been known during the the time your setup was installed:
1- vCAC 6.x VAMI Root account time bomb.
In vCAC 6.x There is a one year expiration time bomb in the VAMI Root account. This will prevent you from logging in to the VAMI consoles. To fix run this command…
# chage –M 99999 root
This will change the timeout and should prevent future issues. This occurs in both the vCAC Identity Appliance , and the vCAC Appliance.
2- vCAC 6.x SSO internal tenant admin password time bomb.
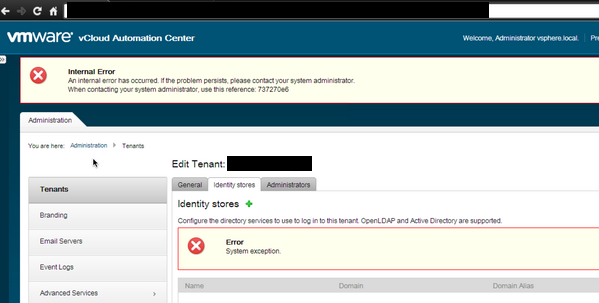
In this particular issue, after setting up vCAC and setting up your tenants and connect it to particular identity source and provide permissions to tenant admins and users and things happily working as expected for the first 90 days. After 90 days, you will discover that you cannot login to any tenant using your tenant admin or tenant user credentials while you are sure these credentials are correct, you would receive an error similar to the below screenshot:
This issue occurs due to expiry of Tenant admins/users passwords after 90 days. By default, the SSO internal tenant admin password expires in 90 days. This password expiration value can be changed or password expiration disabled. After the password expires, the authentication server cannot log in with the old password.
Note: This issue is internal to vRealize related SSO authentication and does not affect external OpenLDAP, Active Directory, or other LDAP configurations.
Note: The current workflow User Interface does not provide any notification when the password is to expire.
Note: This particular time bomb issue has been resolved in 6.1 and above as long you are doing a fresh install, but it persist if you are doing in place upgrade.
Note: If you are not sure about performing the steps below, file a support request with VMware Technical Support and note this Knowledge Base article ID (2075011) in the problem description. For more information on filing a Support Request, see Filing a Support Request in My VMware (2006985).
VMware vRealize Automation using vCenter Single Sign-On (SSO) for tenant authentication
If VMware vRealize Automation is using vCenter Single Sign-On (SSO) for tenant authentication, perform these steps to disable password expiration:
Note: Replace tenant_name with the URL name of your tenant.
- Open an SSH connection to vCenter Server.
- Disable password expiration by running this command:
/opt/likewise/bin/ldapmodify -H ldap://localhost:11711 -x -D "cn=administrator,cn=users,dc=vsphere,dc=local" -W <<EOFResponse: modifying entry “cn=DCAdmins,cn=builtin,dc=vsphere,dc=local”Note: You are prompted for the administrator@vsphere.local password when running this command.
dn: cn=DCAdmins,cn=builtin,dc=vsphere,dc=local
changetype: modify
add: member
member: cn=administrator,cn=users,dc=tenant_name
EOF - Run this command to reset the account control flag:
/opt/likewise/bin/ldapmodify -H ldap://localhost:11711 -x -D "cn=administrator,cn=users,dc=vsphere,dc=local" -W <<EOFResponse: modifying entry “cn=administrator,cn=users,dc=tenant_name.”Note: You are prompted for the administrator@vsphere.local password when running this command.
dn: cn=administrator,cn=users,dc=tenant_name
changetype: modify
replace: userAccountControl
userAccountControl: 0
EOF
Using SSO in the VMware vRealize Automation Identity Appliance
If you are using SSO in the VMware vRealize Automation Identity Appliance, perform these steps to disable password expiration:
- Download the attached file, kb_2075011_identity_appliance.tar.gz , to your workstation
- Using an SCP client, upload kb_2075011_identity_appliance.tar.gz to /tmp of the VMware vRealize Automation Identity Appliance
- Open an SSH connection to the VMware vRealize Automation Identity Appliance.
- Navigate to the temp directory on the Identity Appliance by running cd /tmp command.
- Extract the contents of kb_2075011_identity_appliance.tar.gz into /tmp by running this command:tar zxvf kb_2075011_identity_appliance.tar.gz
- After contents are extracted, execute 0_run_me script on the Identity Appliance :./0_run_me tenant_nameNote: Replace
tenant_namewith the URL name of your tenant. Use this command as a model:./0_run_me vmware - When prompted, enter the password for Administrator@vsphere.local.
VMware vRealize Automation using Windows installation of vCenter SSO for tenant authentication
If VMware vRealize Automation is using a Windows installation of vCenter Single Sign-On for tenant authentication, perform these steps to disable password expiration:
- Open an elevated command prompt.
- Create a temporary directory by running the command:
mkdir c:\temp - Change directories by running the command:
cd c:\temp - Create the
UserAccountControl.ldiffile in Notepad by running the command:notepad UserAccountControl.ldif - Copy and paste the content below into the file:
dn: cn=administrator,cn=users,dc=tenant_nameNotes:
changetype: modify
replace: userAccountControl
userAccountControl: 0
-
-
- Replace
tenant_namewith the URL name of your tenant. - Ensure you include the hyphen on the last line. (In other words, do not omit the hyphen.)
- Replace
- Save and close the
UserAccountControl.ldiffile. - Create the
PasswordExpiration.ldiffile in Notepad by running the command:notepad PasswordExpiration.ldif - Copy and paste the content below into the file:dn: cn=DCAdmins,cn=builtin,dc=vsphere,dc=local
changetype: modify
add: member
member: cn=administrator,cn=users,dc=tenant_name
–Notes:- Replace
tenant_namewith the URL name of your tenant. - Ensure you include the hyphen on the last line. (In other words, do not omit the hyphen.)
- Replace
- Save and close the
PasswordExpiration.ldiffile. - To modify the user account control configuration and password expiration using the files created earlier in this procedure, run these commands:Note: If the
ldifdeexecutable is not available, run this command to install:ServerManagerCmd -i RSAT-ADDS-Tools
Note: ServerManagerCmd has been deprecated, and is not available in Windows Server 2012. For more information, see Microsoft TechNet.The preceding link was correct as of September 18, 2014. If you find the link is broken, provide feedback and a VMware employee will update the link.- To modify the password expiration, run the command:
ldifde -i -f PasswordExpiration.ldif -s localhost -t 11711 -a "cn=Administrator,cn=Users,dc=vsphere,dc=local" *When prompted, enter the password forAdministrator@vsphere.local. - To modify the user account control configuration, run the command:
ldifde -i -f UserAccountControl.ldif -s localhost -t 11711 -a "cn=Administrator,cn=Users,dc=vsphere,dc=local" *When prompted, enter the password forAdministrator@vsphere.local
- To modify the password expiration, run the command:


Speak Your Mind